Howto:MyApps Cloud - Connecting 3rd-party SIP devices (general considerations)
Applies To
This information applies to
- myApps Cloud v13
- General considerations on 3rd-party SIP devices
Disclaimer
This article is presenting a summary of our experience, connecting 3rd-party devices to the myApps Cloud Platform. As innovaphone is not able to track all changes in functionality or firmware of 3rd-party SIP devices, this document is meant to be an orientation to our certified partners. In any case, we recommended to our partners to verify the functionality of a 3rd-party product. As such innovaphone is not liable for any malfunction of, or caused through a 3rd-party product, even if the respective product is listed in this article.
Requirements to 3-rd party SIP devices, when connecting to the myApps Cloud
- By default, the myApps Cloud service relies on the ICE protocol (according RFC 8445) to establish peer-to-peer media communication between connected 3rd-party SIP devices. Thus, the connecting SIP device has to support STUN, TURN and the ICE mechanism.
- In case ICE and TURN are not supported by the SIP device, the absolute minimum requirement is STUN support (in such case, the respective PBX User Object has to enable Media-Relay). In this scenario the media stream is always routed through the PBX (instead of peer-to-peer routing, when using the default ICE mechanism as described above).
- The following setting for Media relay endpoints is configured by default in the myApps Cloud PBX
- Admin UI > PBX > Config > General
- Nothing may be entered in the field > Media relay endpoints > Firewall public IP !
- The TURN field must be checked !
- This ensures that the innovaphone Cloud Turn server is used for this
- Admin UI > IP4 > General > STUN > TURN Server
- Admin UI > PBX > Config > General
- The innovaphone PBX uses the standardized SIP Digest Access Authentication (according RFC 3261 "The Digest Authentication Scheme") to verify the credentials of any connected 3rd-party SIP device.
- If the selected 3rd-party device does not support this protocol, the Digest Authentication Reply Check can be disabled on the customer PBX, for all incoming SIP connections, with the following commands:
- At the advanced PBX user interface > Maintenance > Diagnostics > Command
!config add TSIP /disable-digest-replay-check!config add SIPS /disable-digest-replay-check!config write!config activate
- If the selected 3rd-party device does not support this protocol, the Digest Authentication Reply Check can be disabled on the customer PBX, for all incoming SIP connections, with the following commands:
- Further the following features should be supported by the device
- To ensure secure data connections, the myApps Cloud relies by default TLS encryption (e.g. SIPS or SIP/TLS). Thus, we recommend to select a 3rd-party SIP device supporting TLS. For this reason, the myApps Cloud platform already includes the root certificates of the following 3-rd party manufacturers:
- Yealink
- Gigaset
- snom
- Telecom Behnke (TFE in combination with specific 3rd-Party MediaRunway "Doorbell-App")
(this list will be extended, step-by-step)
Some more hints for evaluating 3rd party devices can be found in the Things to consider section of Howto:Guidelines for Testing 3rd Party SIP Terminal Devices.
Howto articles, for selected 3-rd party SIP devices
For the following 3-rd party devices, a specific description is available, describing details of the respective configuration:
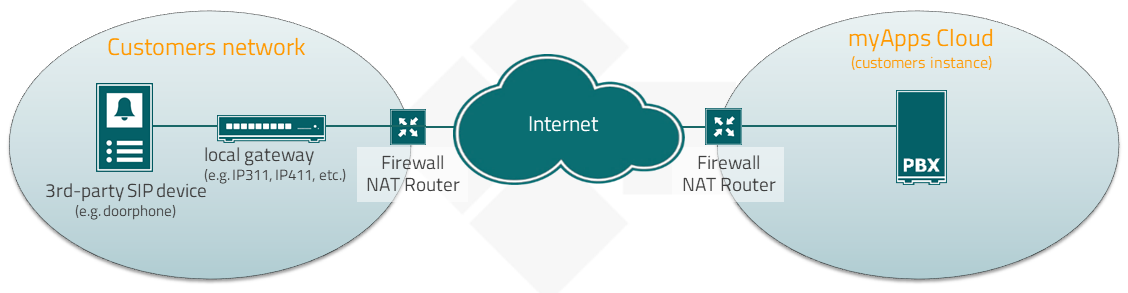
Workaround: 3-rd party SIP devices without STUN support
If a 3rd-party SIP device (e.g. doorphone) does not meet the above defined minimum requirements, an additional local gateway (edge component) on the customers premises is needed, to connect the device to the myApps Cloud platform.