Concept 802.1X: Difference between revisions
(→Info: Customer Feeback: "It is the Authenticator/Authentication Server deciding whether EAP-MD5 or EAP-TLS is going to be applied.") |
m (added section "Debugging") |
||
| Line 15: | Line 15: | ||
*'''Sample Protocol Flow, EAP-TLS:''' | *'''Sample Protocol Flow, EAP-TLS:''' | ||
[[Image:IP240-eap-tls-success.PNG]] | [[Image:IP240-eap-tls-success.PNG]] | ||
=Debugging= | |||
The software module is capable of generating internal trace messages and RPCAP PDUs. Tracing can be enabled by activating a checkmark on the ''/debug.xml'' page of the firmware's web UI. The checkmark is named ''ENET1X0'' (for interface ETH0). The trace buffer can be fetched by a PC connected directly to the PC-port. | |||
=Notes= | =Notes= | ||
<references/> | <references/> | ||
[[Howto:802.1X_EAP-TLS_With_FreeRadius|Howto article: 802.1X EAP-TLS With FreeRadius]] | [[Howto:802.1X_EAP-TLS_With_FreeRadius|Howto article: 802.1X EAP-TLS With FreeRadius]] | ||
Revision as of 16:25, 10 September 2021
Info
802.1X, Port-Based Network Control, is an IEEE standard. The standard allows LAN devices (wired network cabling![1]) to perform an authentication handshake within the 802.3 link layer (Ethernet). The authentication is encapsulated within EAP over LAN (EAPOL) frames. No other traffic, except EAPOL is allowed prior to a successful authentication[2][3].
The standard specifies the following parties participating in an 802.1X authentication:
- Supplicant: The party supplying credentials towards an authenticator on the other side of a point-to-point link. An IP phone fulfills a supplicant's role.
- innovaphones' IP phones are configured to support pass-through of EAPOL messages. A PC attached to the PC-port of a phone may also become a supplicant and may 802.1X-authenticate independently and separately[4].
- Authenticator: The party facilitating the authentication. A switch will usually be the authenticator.
- Authentication Server: The party providing the authentication service to the authenticator. The 802.1X standard mentions a RADIUS server to be an authentication server.
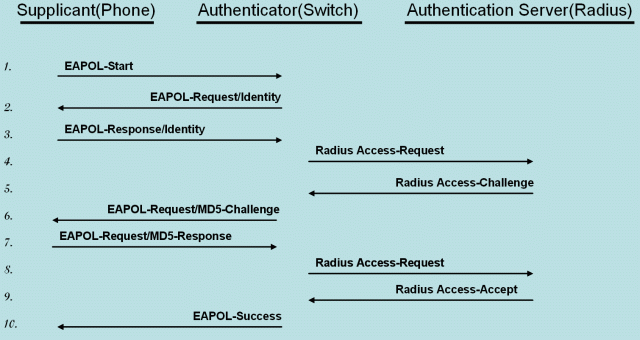
It is the Authenticator/Authentication Server deciding whether EAP-MD5 or EAP-TLS is going to be applied.
- Sample Protocol Flow, EAP-MD5:
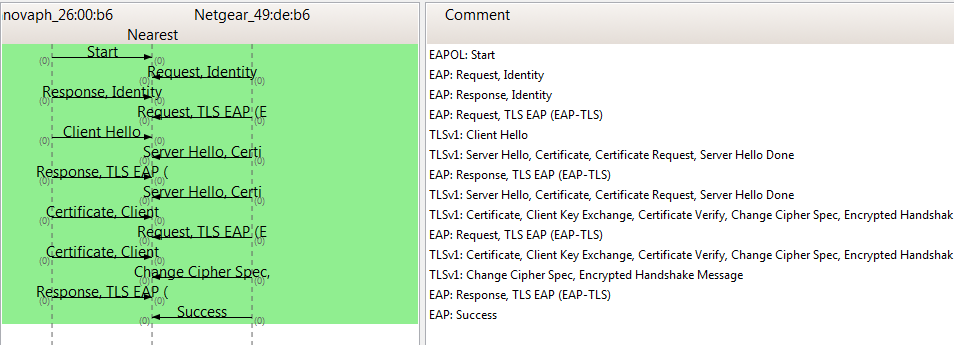
- Sample Protocol Flow, EAP-TLS:
Debugging
The software module is capable of generating internal trace messages and RPCAP PDUs. Tracing can be enabled by activating a checkmark on the /debug.xml page of the firmware's web UI. The checkmark is named ENET1X0 (for interface ETH0). The trace buffer can be fetched by a PC connected directly to the PC-port.
Notes
- ↑ The standard refers to 802 LANs as a whole, including shared media such as 802.11 WLANs. However, only 802.3 LANs are targeted by the functionality discussed in this article.
- ↑ It is an authenticator's task to guarantee that non-EAPOL traffic won't be forwarded before an authentication succeeded.
- ↑ 802.1X must not be considered a bullet-proof security mechanism, since all traffic following the authentication phase is not authenticated.
- ↑ Major authenticators do support multi-auth authentication