Reference7:Certificate management: Difference between revisions
(New section "Device certificate") |
|||
| Line 84: | Line 84: | ||
* Press the "Upload" button. | * Press the "Upload" button. | ||
Please use a PEM file containing the certificate chain from the device certificate up to the root CA certificate. Additionally the file must contain the corresponding private key. | Please use a PEM file containing the certificate chain from the device certificate up to the root CA certificate. Additionally the file must contain the corresponding private key. | ||
Revision as of 11:59, 14 August 2008
Supported certificates
File formats
- DER (Distinguished Encoding Rules, Extensions .crt .cer .der)
- PEM (Personal E-Mail, Extension .pem)
Certificate types
- X.509 versions 1-3
Certificate extensions
- basicConstraints
- keyUsage
- extKeyUsage
- subjectAltName
Note: Validation will fail, if an unsupported extension is marked as critical.
Signing algorithms
- sha1WithRSAEncryption
- md5WithRSAEncryption (only decoding)
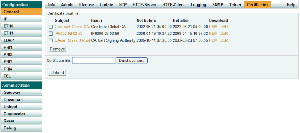
Trust list
This list contains the certificates that should be trusted by the device for TLS connections. Both end-entity and CA certificates can be trusted.
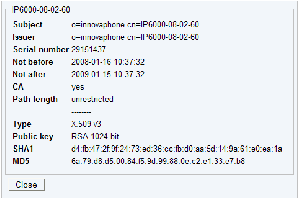
Certificate details
- Click the subject name to view the details.
Installing a certificate from a file
- Select a file.
- Press the "Upload" button.
- Take a look at the certificate details and check wheather the SHA1 and MD5 fingerprints match with the values published by the owner.
Note: PEM files can contain multiple certificates.
Installing a certificate that was rejected before
See section "Rejected certificates".
Removing certificates from the trust list
- Select the items to remove using the checkboxes and press the "Remove" button.
- Open TLS connections that are using these certificates will not be closed.
Download
You can download an individual certificate from the trust list in PEM and DER format by clicking the corresponding link. Additionally you can download the complete list as a text file containing the PEM encoded certificates.
Rejected certificates
This list contains the last 10 certificates that were rejected.
Certificate details
- Click the subject name to view the details.
Clearing the list
- Press the "Clear" button.
Adding rejected certificates to the trust list
- Check the certificate details and decide wheather it should be trusted or not.
- Select certificates using the checkboxes and press the "Trust" button.
Note: Certificates can only be trusted if they are valid (i.e. not expired).
Fast trust list setup in small installations
- Set up your devices without taking care for the trust list
- Clear the list of rejected certificates
- Make a test run (Shouldn't work!)
- Trust the rejected certificates
- Make a test run again (Should work this time!)
Device certificate
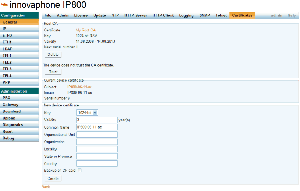
Default certificate
If a device does not have a certificate (e.g. after upgrading from V6) a new private key and self-signed certificate is created automatically. It will contain the netbios name of the device (e.g. IP800-06-11-ac) name and will be valid for 10 years.
- If the certificate is expired, press the "Renew" button to create a new one.
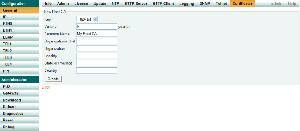
Creating a self-signed certificate
Creating a certificate signing request
Uploading an externally created certificate chain and private key
- Select a file.
- Press the "Upload" button.
Please use a PEM file containing the certificate chain from the device certificate up to the root CA certificate. Additionally the file must contain the corresponding private key.
Device certificate -----BEGIN CERTIFICATE----- MIICMTCCAZqgAwIBAgIBATANBgkqhkiG9w0BAQUFADAVMRMwEQYDVQQDDApNeSBS b290IENBMB4XDTA4MDgxNDA5MDkzM1oXDTExMDgxNDA5MDkzM1owGTEXMBUGA1UE 7HNL76EuQrMmshxYxq0Ay/mlkVc0v7Fp1NzkYn0I2UHpwFZ+zA== -----END CERTIFICATE----- Intermediate CA certificate -----BEGIN CERTIFICATE----- MIICDDCCAXWgAwIBAgIBADANBgkqhkiG9w0BAQUFADAVMRMwEQYDVQQDDApNeSBS 3FSCPvWfh5nk4e8wIAYDVR0OAQEABBYEFE5lzuLAhex3qtxUgj71n4eZ5OHvMA0G CSqGSIb3DQEBBQUAA4GBAAepePqAM59TSoZvSPM/XUn3WKbeOa++6842+4Vp9B1c NmI952d/j/+VsuUXDzPff92IsumPBcch87pksp2GkDrnBvd8WxRsm/n6JF2XS2Ey -----END CERTIFICATE----- Root CA certificate -----BEGIN CERTIFICATE----- MIICDDCCAXWgAwIBAgIBtpmdSuc+WKAS1UZHbtUFADAVEpG4C3G4CQYDVQQDDApe cmKMZ+WFAkEA5e4thgPIFPjLtVL2EK7WxMi2msigZ0HeoBfAJHu5K/H01BqUGdwK hh+ksaW+DStVNG21iuZSQuGwVv56oHj3fQJAdHx+06d7p3G4CA2fdfg24iopluMA oQN9N7Dfw4RyD+ypsMYz8at9RTEqG8Lc0hujGLgtvBpHUp6wxdUuRw4DJQJAGqn0 PYZSvZvcg7qLLoQYA9oC0xBRCahp2MboUVLHtoDok3BBnH4X+lXRE4jU8VIFH39Z -----END CERTIFICATE----- Device private key -----BEGIN RSA PRIVATE KEY----- MIICXAIBAAKBgQDecOKfxrVdHNZRl8RnpNItpmdSuc+WKAS1UZHbtdH5dUJ7OzG3 ZtW684dkm+mbLP00uY4Qiu25dNg0pKp7svihPU8AvKjoyIS52R2Mtt+/hTpjDfgj mGFyhMMmziCLaC+oKL4W88sivv7oOjUlBmGHc0JarKoN1q3Yxgcfg4Zk8QIDAQAB UcVghAbSXJ5G3A3v9POs8UthRMxPrnN2c7DadjZp7Qg= -----END RSA PRIVATE KEY-----
Taking an identity from one device to another
- Click the "Download chain and private key" link and save the file on your PC.
- Upload the file to the new box (see above).
Root certification authority on Compact Flash card
This is the recommended approach to securely deloying PKI to innovaphone gateways.
- The private key of the CA is never being sent over the network or stored on a device.
- You only have to add a single certificate to the trust list of your devices.
Setting up the Root CA
- Insert an empty CF card into the card slot of a gateway.
- Click the "Root CA" link.
- Specify the desired bit strength, validity and distinguished name for the certificate and click the "Create" button.
- Wait until the private key and the certificate have been created.
- Check the certificate details.
- Remove the CF card and keep it at a safe place or continue with creating a device certificate.
Creating a device certificate
- Insert the CF card into the card slot of a gateway.
- Click the "Root CA" link.
- Most probably you want to add the root CA certificate to the trust list of the device. Click the "Trust" button.
- Specify the desired bit strength, validity and distinguished name for the certificate.
- Select "Backup on CF card", if you want to store the newly created private key and certificate on the CF card.
- Click the "Create" button.
- Wait until the private key and the certificate have been created.
- Check the certificate details.
- Remove the CF card and keep it at a safe place.