Reference8:Delegated Authentication
Applies to
All devices with firmware version 8 and later.
Overview
Each device has its own administrator/viewer accounts.
In version 8 and later a single device can act as an authentication server for the rest of the devices. User accounts that are managed on the authentication server can be used to login on each device in the installation. You can also configure devices to accept user accounts from a Windows domain.
How it works
Version 8 devices can use Kerberos to authenticate users that are not managed locally but on a remote Kerberos server.
Kerberos
A Kerberos server manages users and services for a realm that is specified by a distinct name. It shares a secret password with each user and each service. Users can obtain a ticket for a service from the Kerberos server if they proove that they know their own password. Services can then authenticate users by validating tickets instead of passwords. Therefore many devices can be accessed using the same user credentials but only the Kerberos server and the user have to know it.
Logging in
The main idea of how the centralized login process works is the following:
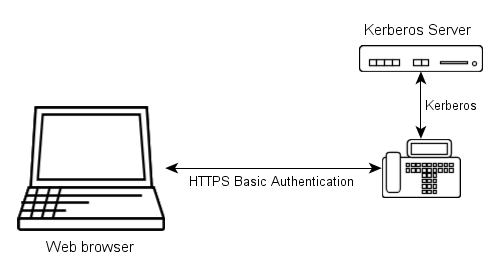
- The browser sends user name and password to the box, using HTTP basic authentication.
- The box then uses Kerberos to obtain a ticket on behalf of the user from the Kerberos server for its own web server.
If that was successful the password is valid and the user is authenticated. The ticket also contains some information whether the user is an administrator or a viewer.
Local and remote users
To distinguish between local users and users of a Kerberos realm, the realm has to be prepended to the user name, separated by a backslash ('\')
Example:
- Local user: admin
- Remote user: REALM\radmin
Security considerations
Use HTTPS
As HTTP basic authentication transmits plaintext passwords, the use of HTTPS is mandatory. Please disable normal HTTP access to the devices or enable Force HTTPS.
Use local users only for recovery purposes
Although the old local user accounts of devices can still be used to login, this should not be done.
We recommend to choose a different secure administrator password for each device. After Single Sign-On has been configured, the list of admin passwords should be locked away and used only for recovery purposes. From this time only user accounts from the Kerberos realm should be used to access devices.