Reference11r2:Interfaces/ETH/802.1X
Info
802.1X, Port-Based Network Control, is an IEEE standard. The standard allows LAN devices (wired network cabling![1]) to perform an authentication handshake within the 802.3 link layer (Ethernet). The authentication is encapsulated within EAP over LAN (EAPOL) frames. No other traffic, except EAPOL is allowed prior to a successful authentication[2][3].
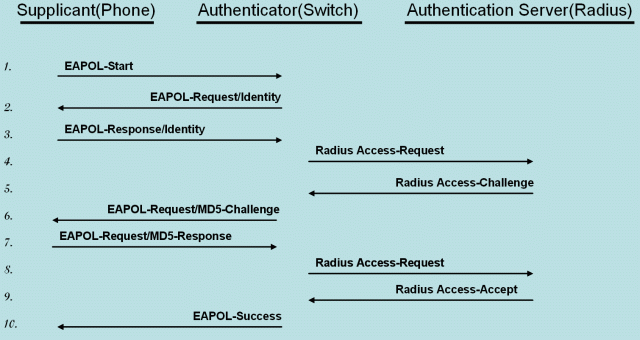
The standard specifies the following parties participating in an 802.1X authentication:
- Supplicant: The party supplying credentials towards an authenticator on the other side of a point-to-point link. An IP phone fulfills a supplicant's role.
- innovaphones' IP phones are configured to support pass-through of EAPOL messages. A PC attached to the PC-port of a phone may also become a supplicant and may 802.1X-authenticate independently and separately[4].
- Authenticator: The party facilitating the authentication. A switch will usually be the authenticator.
- Authentication Server: The party providing the authentication service to the authenticator. The 802.1X standard mentions a RADIUS server to be an authentication server.
- Sample Protocol Flow, EAP-MD5:
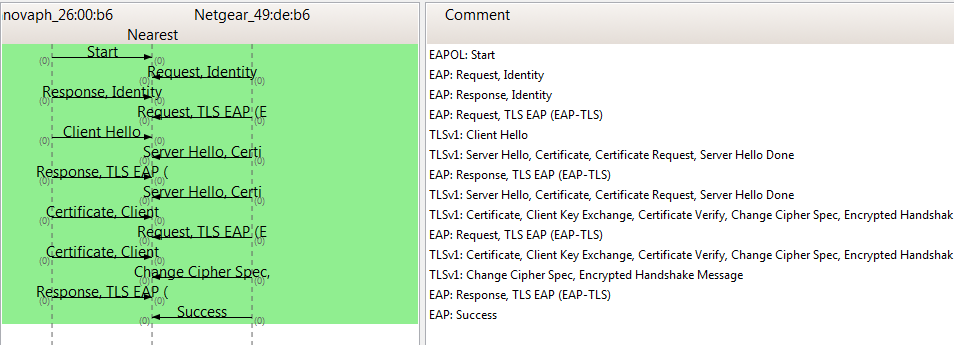
- Sample Protocol Flow, EAP-TLS:
Configuration
EAP-MD5
- User Enter the user/identity to authenticate with.
- Password Enter the shared secret for the MD5 challenge/response handshake.
EAP-TLS
- User Enter the user/identity[5] to be sent within the EAP Identity request.[6]
- Password Enter arbitrary content.[6]
- General/Certificates/Device Certificate[7]
- Utilize the innovaphone manufactured device certificate, signed by the innovaphone CA.
- The innovaphone CA certificate must then be employed as a trusted CA at the authentication server(e.g.: FreeRadius)
- Or upload an otherwise handcrafted device certificate to authenticate with at the authenticator.
- The certificate must have it's private key aboard. A concatenated PEM-format certificate with the key appended will do. In principle.:
- The certificate must have it's private key aboard. A concatenated PEM-format certificate with the key appended will do. In principle.:
- Utilize the innovaphone manufactured device certificate, signed by the innovaphone CA.
BEGIN CERTIFICATE-----
MIICxzCCAjCgAwIBAgIBAzANBgkqhkiG9w
...
MVDEBAuPOHunKSoHcpxrlPJQ==
END CERTIFICATE-----
BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQCX8OyuGH2lP39juhv+Tm4Qa
...
f9/z8tG
END RSA PRIVATE KEY-----
Proxy-Logoff
If the phone's LAN-port got disconnected, EAPOL-Logoff messages are going to be sent on behalf of participants connected to the phone's PC-port. An EAPOL-Logoff will be sent for each MAC-address learned from traversing EAPOL-Start messages.
Notes
- ↑ The standard refers to 802 LANs as a whole, including shared media such as 802.11 WLANs. However, only 802.3 LANs are targeted by the functionality discussed in this article.
- ↑ It is an authenticator's task to guarantee that non-EAPOL traffic won't be forwarded before an authentication succeeded.
- ↑ 802.1X must not be considered a bullet-proof security mechanism, since all traffic following the authentication phase is not authenticated.
- ↑ Major authenticators do support multi-host authentication
- ↑ EAP-TLS doesn't mandate that identity to necessarily be the same as the certificates subject/CN
- ↑ 6.0 6.1 A non-empty user/password just serves as an "on"-switch
- ↑ The server certificate won't be validated