Howto16r1:Configure OAuth2 E-Mail: Difference between revisions
No edit summary |
No edit summary |
||
| Line 102: | Line 102: | ||
For other e-mail providers the client secret post OAuth2 flow may be configured in a generic way. Details need to be supplied by the e-mail provider. | For other e-mail providers the client secret post OAuth2 flow may be configured in a generic way. Details need to be supplied by the e-mail provider. | ||
For the Microsoft 365 setup above it would be as follows with | |||
Token endpoint: ''<nowiki>https://login.microsoftonline.com/af326a34-169c-469e-946b-1ef57925306b/oauth2/v2.0/token</nowiki>'' | |||
Authorization URL: ''<nowiki>https://login.microsoftonline.com/af326a34-169c-469e-946b-1ef57925306b/oauth2/v2.0/authorize?scope=https://outlook.office.com/SMTP.Send</nowiki> offline_access'' | |||
[[File:OAuth2ClientSecretPost.png|none|thumb|600x600px|/OAuth2ClientSecretPost.png|/OAuth2ClientSecretPost.png]] | [[File:OAuth2ClientSecretPost.png|none|thumb|600x600px|/OAuth2ClientSecretPost.png|/OAuth2ClientSecretPost.png]] | ||
For the Gmail example above the generic confguration would be like this with | |||
The private key jwt OAuth2 flow can be configured generically as well. | The private key jwt OAuth2 flow can be configured generically as well. | ||
[[File:OAuth2PrivateKeyJWT.png|none|thumb|600x600px|/OAuth2PrivateKeyJWT.png|/OAuth2PrivateKeyJWT.png]] | [[File:OAuth2PrivateKeyJWT.png|none|thumb|600x600px|/OAuth2PrivateKeyJWT.png|/OAuth2PrivateKeyJWT.png]] | ||
Revision as of 07:49, 5 October 2025
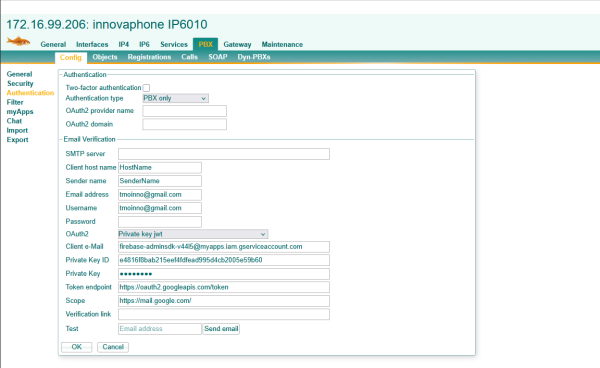
innovaphone PBX and apps can be configured to send E-Mails for various subjects and purposes. Major E-Mail providers intent to discontinue the username/password authentication schemes in favour of OAuth2. PBX and Apps version 16r1 does support OAuth2 authentication for SMTP. Here is a step by step guide how to set up OAuth2 support in Microsoft 365 through the Azure Portal and how to set it up on a Google Gmail account in the Google Cloud Console.
Microsoft 365
Log in to Microsoft Azure Portal (https://portal.azure.com) and go to Microsoft Entra ID.
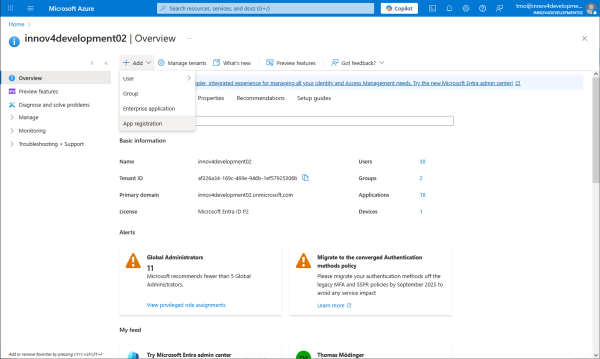
Add a new app registration to create client credentials.
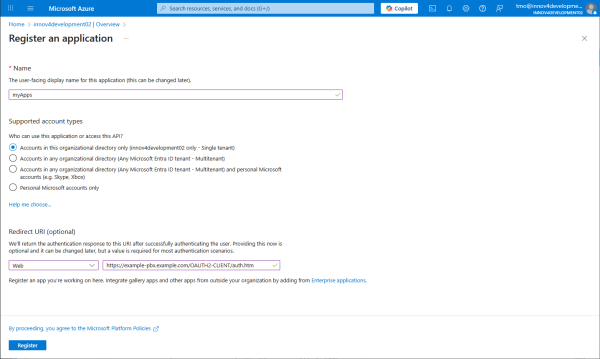
Register the application and maybe already fill in the redirect URI for Web based application type to path OAUTH2-CLIENT/auth.htm at the PBX.
App registration is complete. Client ID and tenant needs to be configured at the PBX and every app that will be sending e-mails.

Create a client secret.
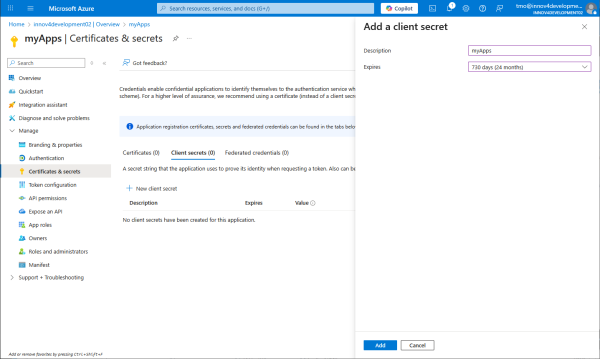
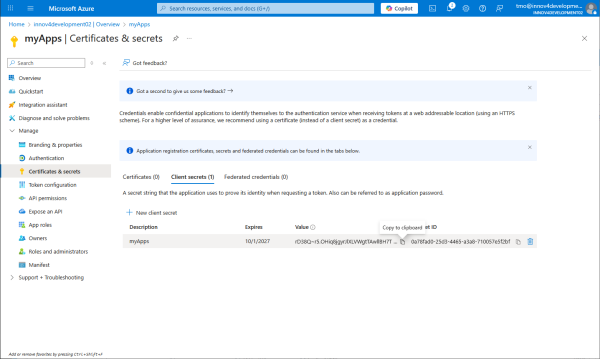
Copy the client secret. It also needs to be configured at the PBX and every app that will be sending e-mails.
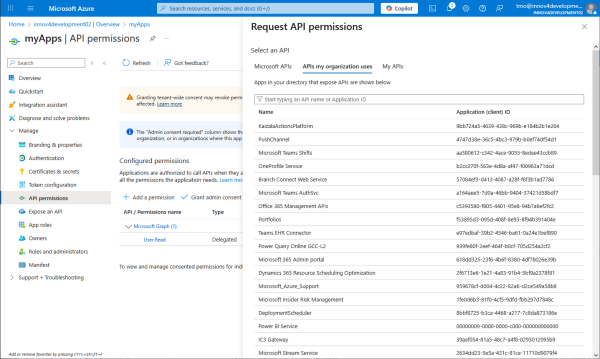
Add permissions located in APIs my organization uses.
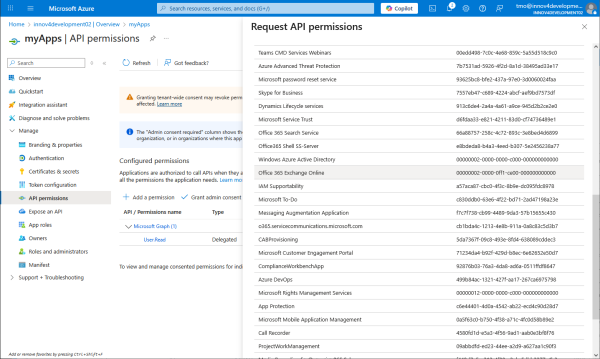
More precisely located in Office 365 Exchange Online.
And there in the application permissions.
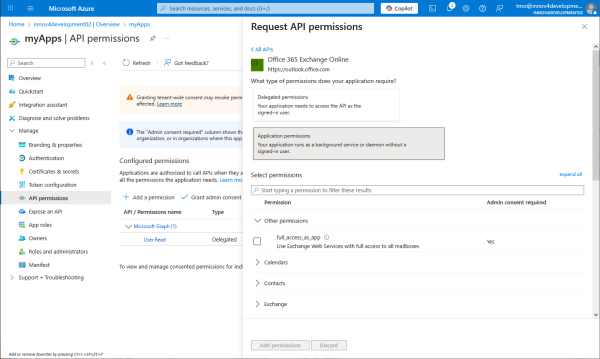
Namely SMTP Mail.Send.
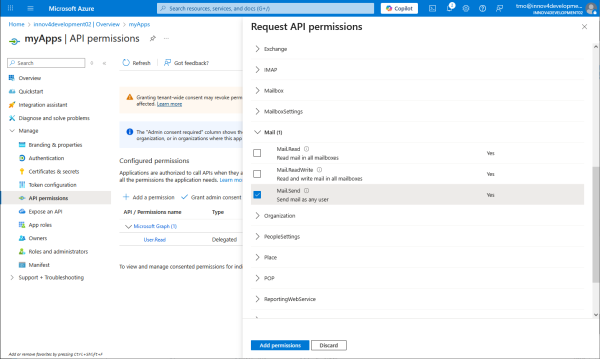
Grant admin permission for Mail.Send.
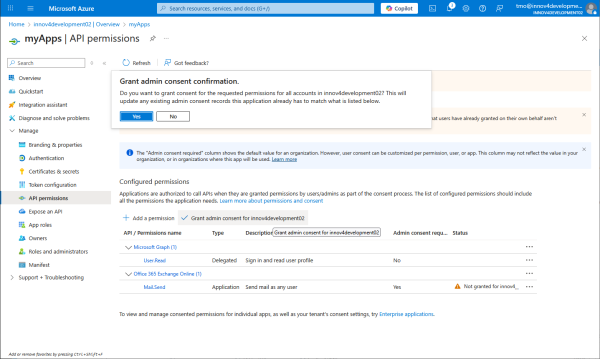
API permissions are now granted.
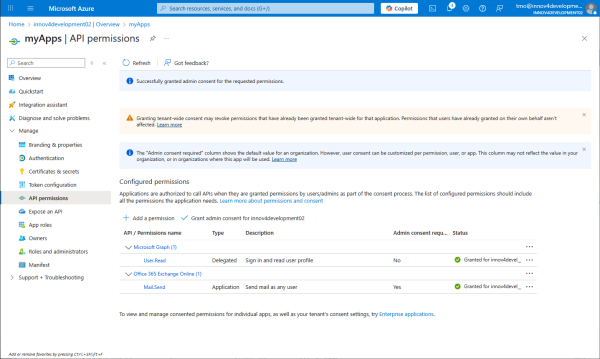
Tell all redirect URIs that the PBX and the apps will be using during interactive authorization.
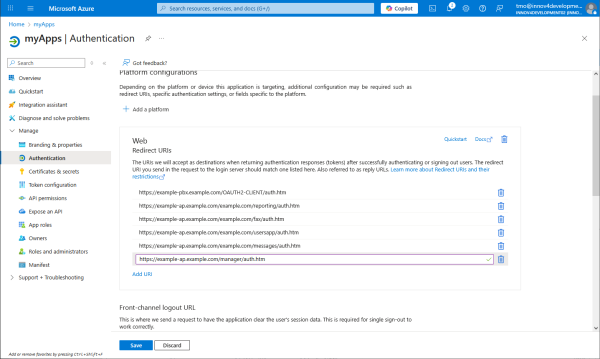
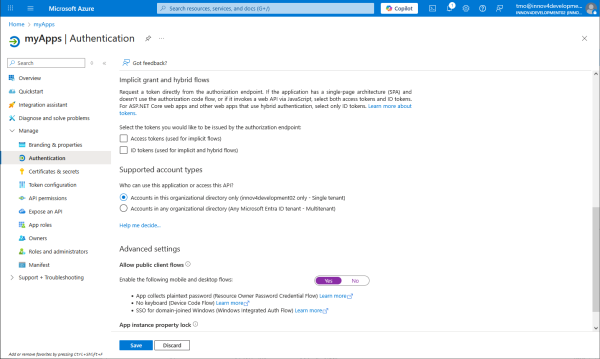
Allow public client flows of OAuth2. Resource Owner Password Credentials Flow has the advantage that it doesn't need interactive authorization.
Log in to the Microsoft 365 admin center (https://admin.cloud.microsoft).
Make sure that Microsoft 365 licenses are assigned to your user.
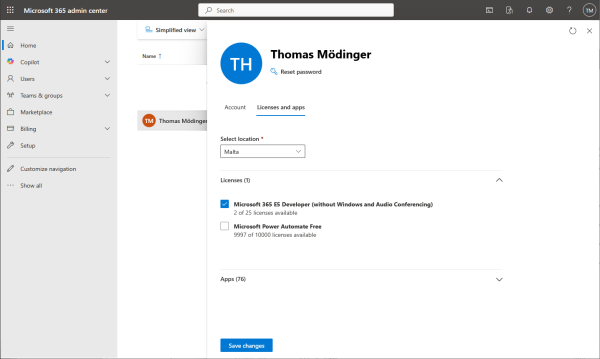
Set your user active.
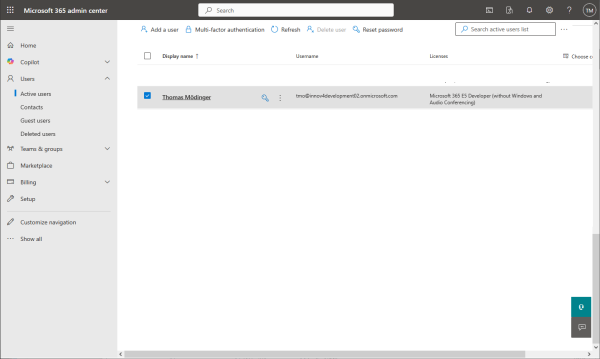
Locate the Mail tab of your user.
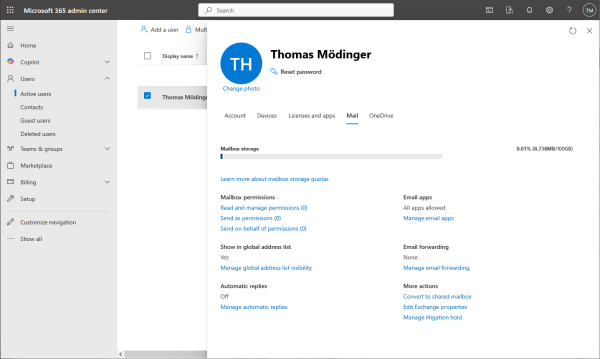
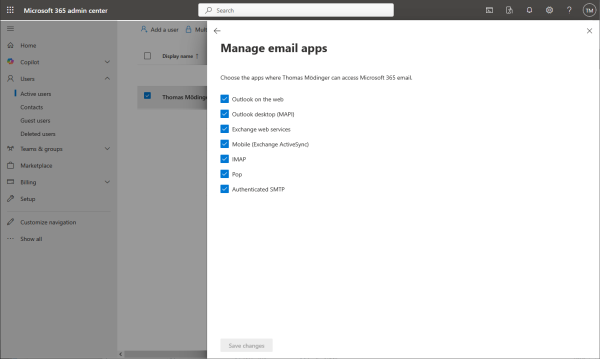
Allow authenticated SMTP.
Login to the Exchange admin center (https://admin.exchange.microsoft.com).
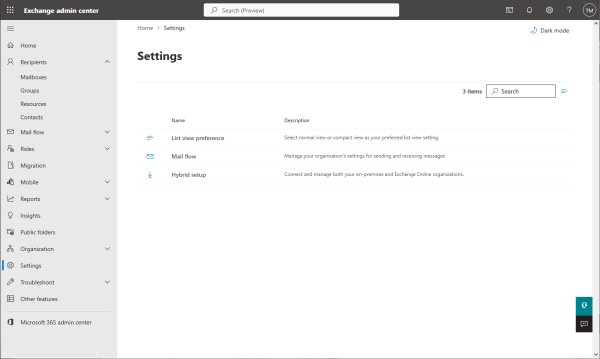
Remove deactivation of the SMTP AUTH protocol.
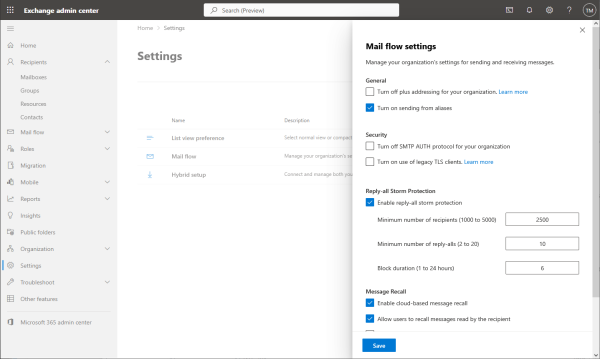
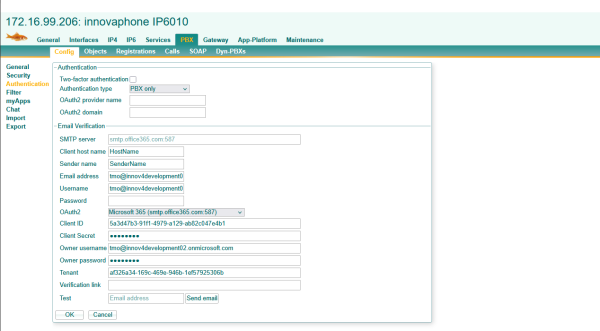
With this Microsoft setup the OAuth2 configuration for the resource owner password credentials flow can be filled in as follows.
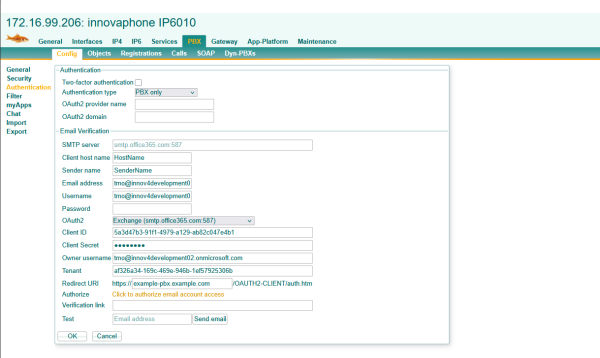
For interactive authorization this is the OAuth2 configuration. Authorize e-mail access one time and send a test mail to verify everything went well.
Gmail
Login to the Google Cloud Console (https://console.cloud.google.com), select a project, New project.
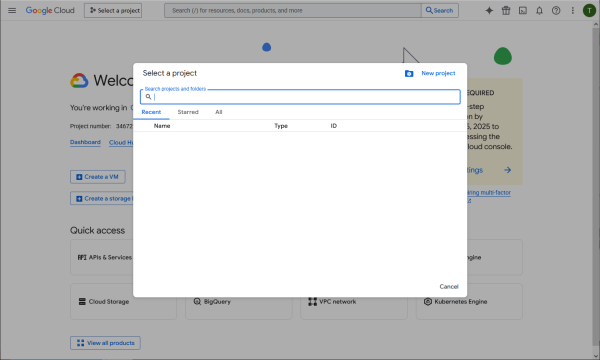
Create the project.
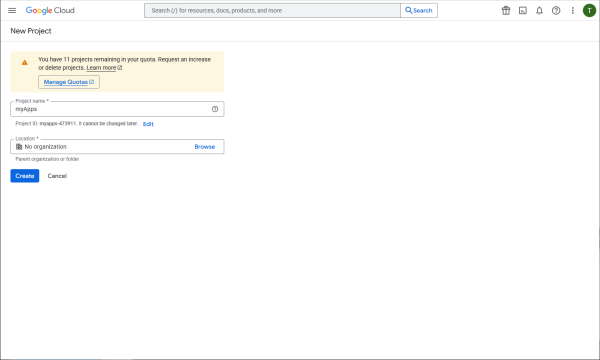
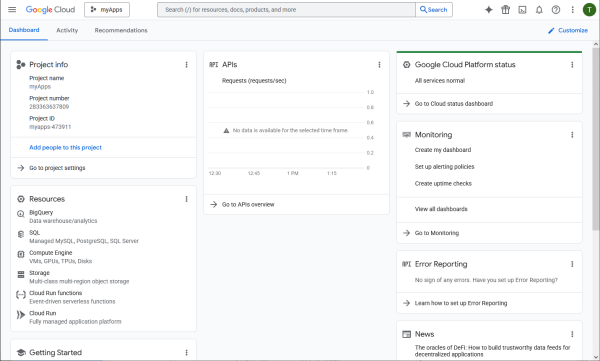
Client credentials will be created in this project.
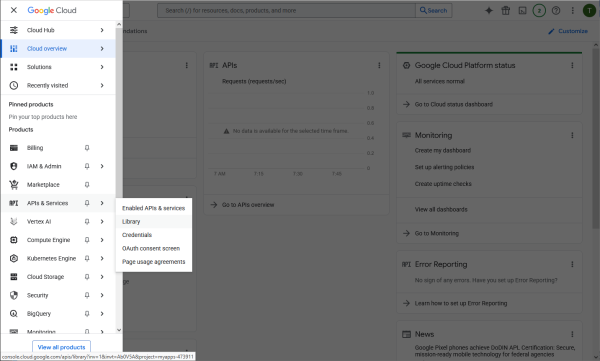
From the library specify the APIs needed to access.
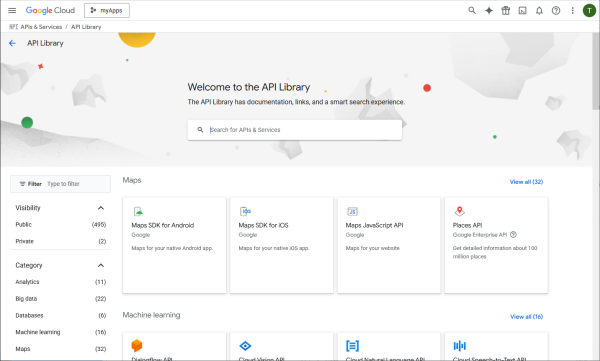
These are in the Gmail API.
Choose the Gmail API and enable it.
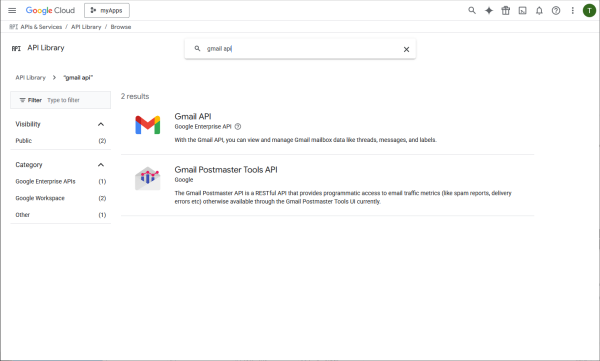
Credentials need to be created.
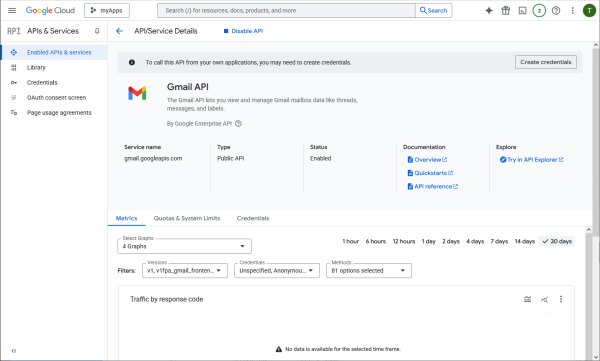
Invoke the help me choose wizard.
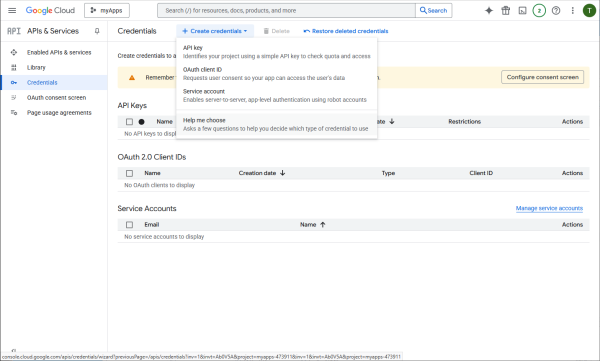
User data access is needed.
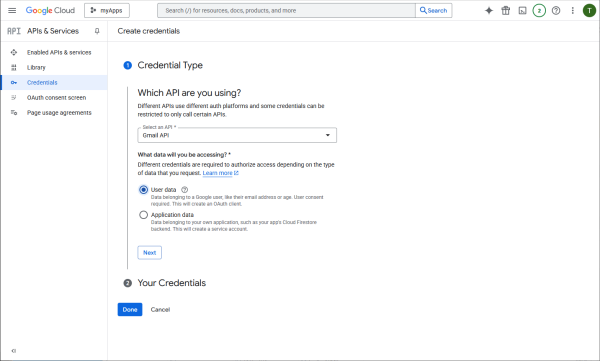
Configure the consent screen of the interactive authorization.
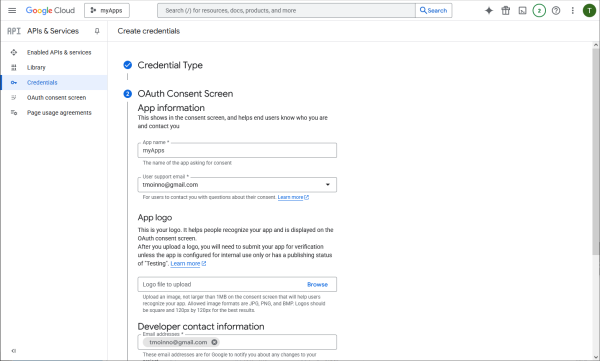
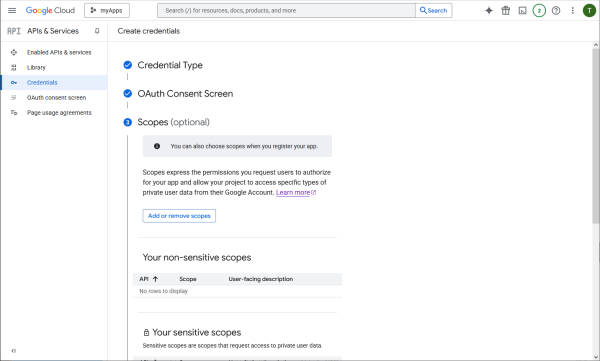
Specify the permissions that need to be authorized by the user.
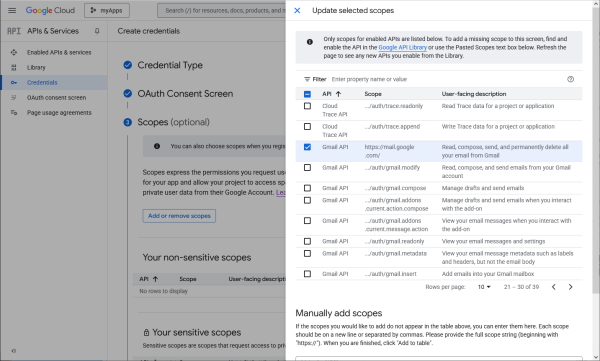
Its mail.google.com in general.
And its to send email on the users behalf.
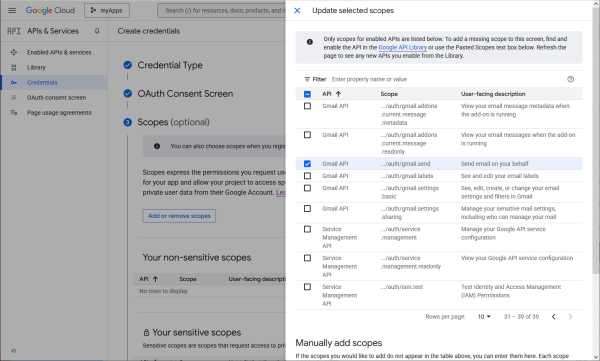
These are the scopes needed.
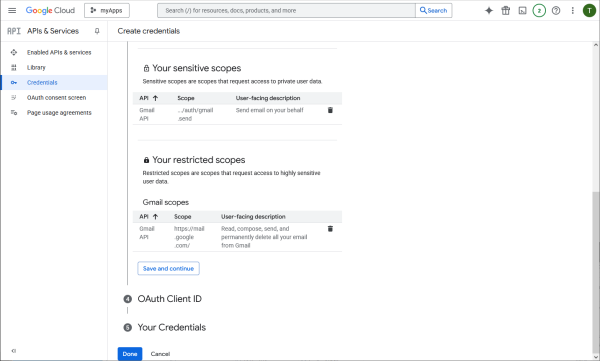
Ask client credentials for Web type application.
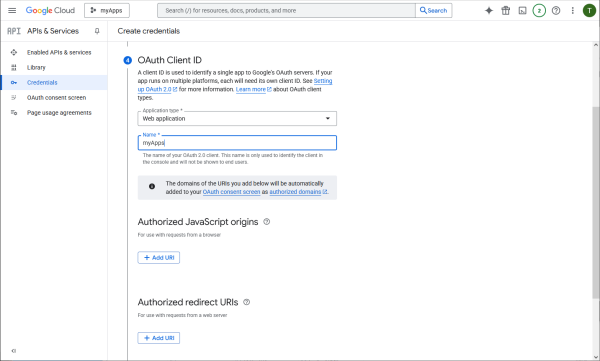
Tell all redirect URIs that the PBX and the apps will be using during interactive authorization.
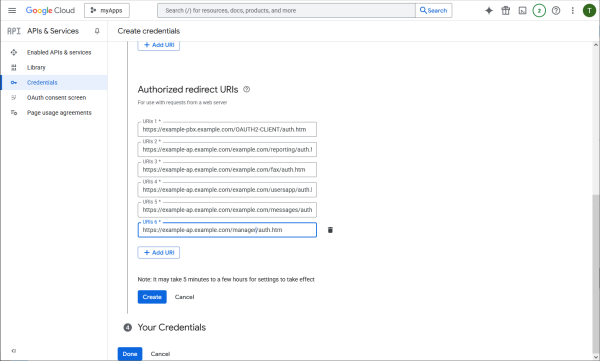
Download the credentials. This json file contains all information for OAuth2 configuration.
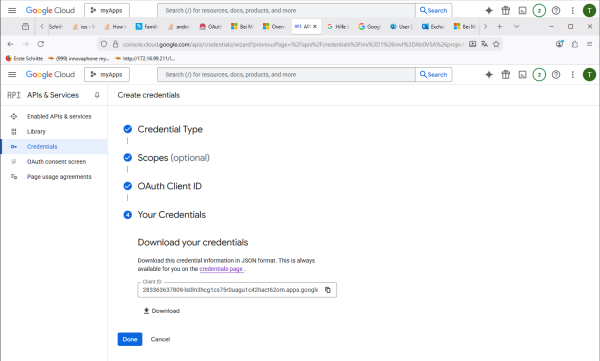
Customize the OAuth consent screen
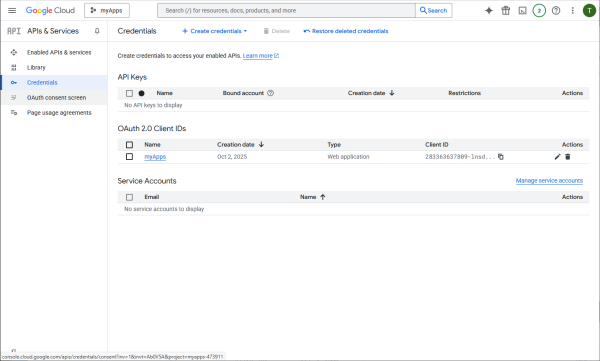
Start the customization wizard.
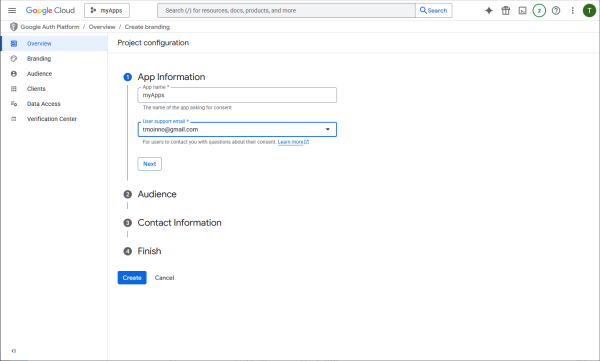
Choose which users may authorize.
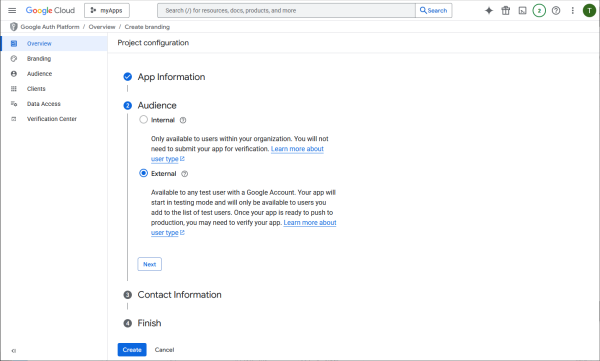
Google workspace users may choose internal audience. Users not in Google workspace proceed with external.
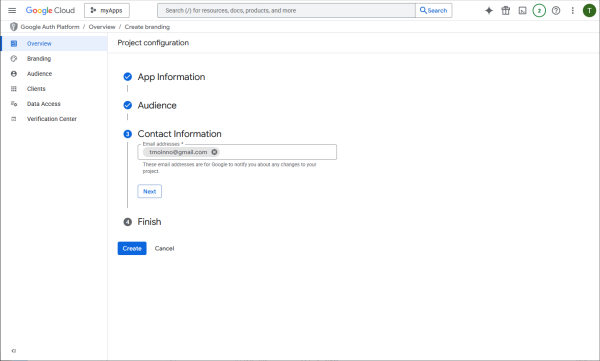
Add a test user.
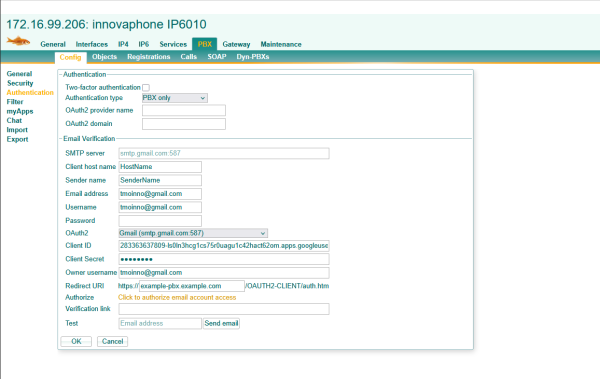
The OAuth2 parameters can be filled in with the information from the json file downloaded above. Authorize e-mail access one time and send a test mail to verify everything went well.
Generic
For other e-mail providers the client secret post OAuth2 flow may be configured in a generic way. Details need to be supplied by the e-mail provider.
For the Microsoft 365 setup above it would be as follows with
Token endpoint: https://login.microsoftonline.com/af326a34-169c-469e-946b-1ef57925306b/oauth2/v2.0/token
Authorization URL: https://login.microsoftonline.com/af326a34-169c-469e-946b-1ef57925306b/oauth2/v2.0/authorize?scope=https://outlook.office.com/SMTP.Send offline_access
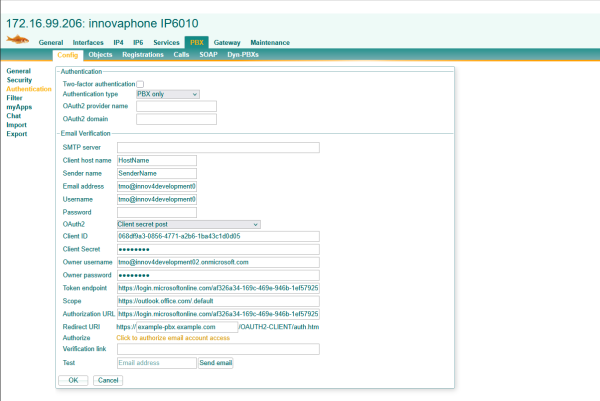
For the Gmail example above the generic confguration would be like this with
The private key jwt OAuth2 flow can be configured generically as well.