Howto:Sign an innovaphone certificate request using a 3rd party CA
Applies To
This information applies to
- All innovaphone devices
- firmware v9hotfix2
More Information
Problem Details
A certificate can contain a KeyUsage and a ExtendedKeyUsage entry. This defines the purpose of this certificate and the tasks that this certificate can be used for. For example a certificate used in a MTLS - connection, should have the entries:
- KeyUsage:
- digital_signature
- key_encipherment
- ExtendedKeyUsage:
- server_authentication
- client_authentication
The KeyUsage and the ExtendedKeyUsage attributes can be set by two instances:
- the device issuing the certificate request, i.e. the innovaphone device
- the device that creates the certificate, i.e. the 3rd party CA
Until v9hotfix2 innovaphone devices did not set this KeyUsage and ExtendedKeyUsage attributes, when creating a certificate request. It depended only on the CA, if the resulting certificate would have the correct KeyUsage and ExtendedKeyUsage attributes. Some CAs however do not change this attributes, this results in a certificate without KeyUsage and ExtendedKeyUsage attributes. The resulting certificate could then be rejected by other TLS - endpoints.
Starting with v9hf2, innovaphone devices set the KeyUsage and ExtendedKeyUsage attributes with a set of values that enable the certificate to be used in client and server authentication scenarios. The remainder of this article, will contain hints on how to create a certificate using different CA applications.
Windows 2008/2003 Server Standard Edition
The CA offered on the Standard Edition server has no possibility to change the KeyUsage and ExtendedKeyUsage attributes. It will just sign the KeyUsage and ExtendedKeyUsage attributes contained in the certificate signing request. When using a firmware version prior to v9hf1, this will result in a certificate with empty KeyUsage and ExtendedKeyUsage attributes and the problem described in the section before.
Starting with v9hf2, the certificate signing request as well as the resulting certificate contains all needed KeyUsage and ExtendedKeyUsage attributes.
Windows 2008/2003 Server Enterprise Edition
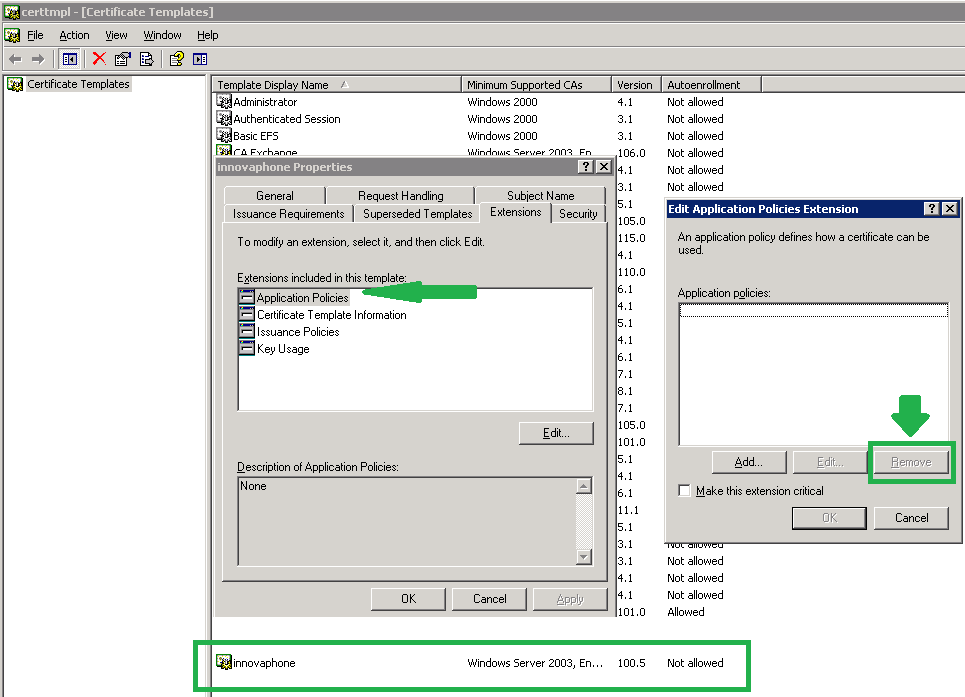
The CA offered on the Enterprise Edition server has the possibility to change the KeyUsage and ExtendedKeyUsage attributes, by using so-called 'Certificate Templates'. However since the certificate signing request has already all needed information, the risk is that the 'Certificate Templates' misconfigures and overwrites a KeyUsage and ExtendedKeyUsage attribute set by the issuing innovaphone device.
Therefore it is best to not use the 'Certificate Templates' at all. In case that this is not possible, you should create a 'Certificate Templates' with no KeyUsage and ExtendedKeyUsage attributes. This 'empty' 'Certificate Template' will not overwrite any settings received from the certificate signing request.
A documentation on how to create a 'Certificate Template' is found here: [1]
After you created the certificate template, delete all entries found in Extensions->Application Policies and Extensions->Key Usage. The screenshot below shows such an empty 'Certificate Template'.