Howto:Tracing from Trapeze Access Points to Wireshark: Difference between revisions
m New page: ==Applies To== This information applies to * Trapeze WLAN Infrastucture (e.g. MXR-2) ==Summary== This is a quick a dirty introduction to setting up a Trapeze management switch for traci... |
|||
| (12 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
==Applies To== | ==Applies To== | ||
This information applies to | This information applies to | ||
* Trapeze WLAN Infrastucture (e.g. MXR-2) | * Trapeze WLAN Infrastucture (e.g. MXR-2) (Firmware > 7.0.13.3.0) | ||
* Wireshark (Version > 1.1.2) | |||
* IP72 | |||
==Summary== | ==Summary== | ||
This is a quick a dirty introduction to setting up a Trapeze management switch for tracing all 802.11 traffic to a Wireshark running on a PC. For complete and official documents, | This is a quick a dirty introduction to setting up a Trapeze management switch for tracing all 802.11 traffic to a Wireshark running on a PC. | ||
For complete and official documents, please visit http://www.trapezenetworks.com. | |||
For Wireshark documents, please visit http://www.wireshark.org/. | |||
==Settings== | ==Settings== | ||
Login to a switch through SSH, here the login transcript: | Login to a Trapeze management switch through SSH, here the login transcript: | ||
login as: admin | login as: admin | ||
Copyright (c) 2002 - 2009 Trapeze Networks, Inc. All rights reserved. | Copyright (c) 2002 - 2009 Trapeze Networks, Inc. All rights reserved. | ||
Username: admin | Username: admin | ||
Password: | Password: | ||
*trapeze-inno> enable | |||
Enter password: | |||
*trapeze-inno> | Setup a listener called "mysnoop", make sure to use the address of a local PC running Wireshark instead of 192.168.1.10 | ||
*trapeze-inno# | |||
*trapeze-inno# set trace dot1x level 9 | |||
success: change accepted. | |||
*trapeze-inno# set snoop mysnoop observer 192.168.1.10 | |||
success: change accepted. | |||
*trapeze-inno# set snoop map mysnoop ap 1 radio 1 | |||
success: change accepted. | |||
Repeat this for all access points, e.g. if 3 APs are being managed by the switch, proceed with: | |||
*trapeze-inno# set snoop map mysnoop ap 2 radio 1 | |||
success: change accepted. | |||
*trapeze-inno# set snoop map mysnoop ap 3 radio 1 | |||
success: change accepted. | |||
Finally, start tracing: | |||
*trapeze-inno# set snoop mysnoop mode enable | |||
success: change accepted. | |||
*trapeze-inno# | |||
Now start Wireshark on the PC 192.168.1.10. | |||
Capture->Options: | |||
* Capture packets in promiscuous mode set. | |||
* Capture Filter: '''port 37008''' | |||
* Start | |||
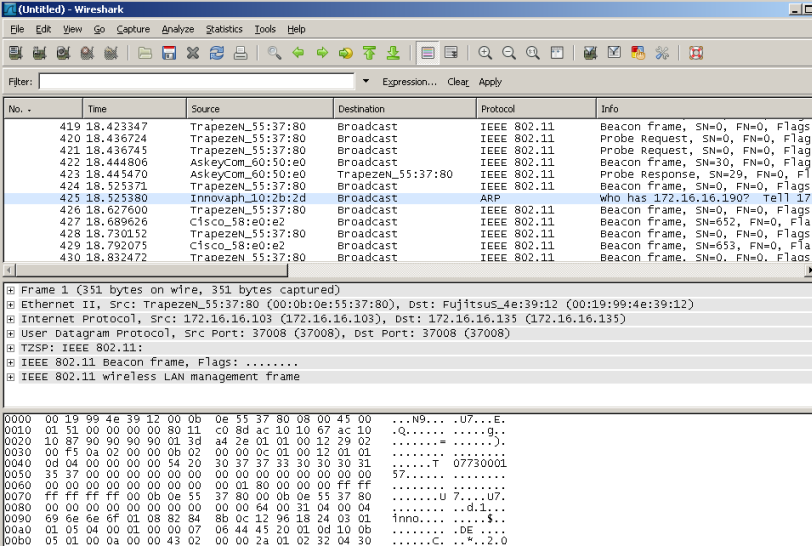
Check if ok, try to locate e.g a beacon packet in Wireshark window. | |||
[[image:Wireshark-scoop.png]] | |||
Disable listener; this stops the scoop. | |||
*trapeze-inno# set snoop mysnoop mode disable | |||
success: change accepted. | |||
When done, don't forget to delete the listener: | |||
clear snoop mysnoop | |||
Latest revision as of 18:02, 4 December 2009
Applies To
This information applies to
- Trapeze WLAN Infrastucture (e.g. MXR-2) (Firmware > 7.0.13.3.0)
- Wireshark (Version > 1.1.2)
- IP72
Summary
This is a quick a dirty introduction to setting up a Trapeze management switch for tracing all 802.11 traffic to a Wireshark running on a PC. For complete and official documents, please visit http://www.trapezenetworks.com. For Wireshark documents, please visit http://www.wireshark.org/.
Settings
Login to a Trapeze management switch through SSH, here the login transcript:
login as: admin Copyright (c) 2002 - 2009 Trapeze Networks, Inc. All rights reserved. Username: admin Password: *trapeze-inno> enable Enter password:
Setup a listener called "mysnoop", make sure to use the address of a local PC running Wireshark instead of 192.168.1.10
*trapeze-inno# *trapeze-inno# set trace dot1x level 9 success: change accepted. *trapeze-inno# set snoop mysnoop observer 192.168.1.10 success: change accepted. *trapeze-inno# set snoop map mysnoop ap 1 radio 1 success: change accepted.
Repeat this for all access points, e.g. if 3 APs are being managed by the switch, proceed with:
*trapeze-inno# set snoop map mysnoop ap 2 radio 1 success: change accepted. *trapeze-inno# set snoop map mysnoop ap 3 radio 1 success: change accepted.
Finally, start tracing:
*trapeze-inno# set snoop mysnoop mode enable success: change accepted. *trapeze-inno#
Now start Wireshark on the PC 192.168.1.10.
Capture->Options:
- Capture packets in promiscuous mode set.
- Capture Filter: port 37008
- Start
Check if ok, try to locate e.g a beacon packet in Wireshark window.
Disable listener; this stops the scoop.
*trapeze-inno# set snoop mysnoop mode disable success: change accepted.
When done, don't forget to delete the listener:
clear snoop mysnoop